Web technology detection and fingerprinting in Invicti
Dynamic security testing for web applications focuses on finding exploitable vulnerabilities in a running application. But even if your own code is secure, it is only the uppermost layer of a web technology stack that can present malicious actors with many other opportunities for attack. Learn how Invicti identifies vulnerable technologies to present a complete picture of your web application security.
Your Information will be kept private.
Begin your DAST-first AppSec journey today.
Request a demo
The Achilles’ heel of modern web applications
Modularity is crucial for rapid software development, so it is no surprise that today’s web applications can contain as little as 10% of custom code. The rest is scaffolding: frameworks, libraries, and external components that do the heavy lifting so application developers can focus on business logic. This is especially important in agile development, where work is divided into smaller parts that need to be completed in a matter of weeks. The shift from monolithic to modular applications has also affected application security. The growing awareness that security needs to be an integral part of the software development lifecycle (SDLC) means that custom application code usually goes through some sort of security testing to catch at least the most obvious security flaws. But since custom code is only one part of the total attack surface, attackers are increasingly turning their attention to weaknesses in the underlying technologies. This is where the reliance on convenient ready-made components becomes a liability. Today’s web applications, including commercial products, combine custom code and open-source components, with the latter commonly making up from 70% to 90% of the codebase. The problem is that as many as 79% of applications use libraries that are never updated after being included in the code, not even for critical security updates. Many of these components are used in thousands of applications worldwide, making it easy for attackers to find installations that use known vulnerable libraries. This is the web application aspect of supply chain vulnerabilities that were called out in Joe Biden’s recent presidential order as a priority area for cybersecurity.Finding the many ways you can be vulnerable
Dynamic application security testing (DAST) solutions probe a running application for weaknesses. To accurately mimic the actions of real-life attackers, advanced products such as Invicti don’t stop at scanning your application for vulnerabilities but also detect its underlying technologies. Apart from using a cutting-edge heuristic scanning engine to detect previously unknown vulnerabilities, Invicti also has its own vulnerability database for reporting out-of-date libraries, frameworks, and other application components. The vulnerability database (VDB) brings together all of Invicti’s security checks and serves as a repository of known web technologies along with their versions and security status. The VDB is carefully curated by Invicti’s security researchers and periodically updated based on multiple sources of vulnerability intelligence to ensure that the latest web application CVEs and other known issues are covered. VDB updates are automatically reflected in the Invicti user interface and available for use in your scan policies.3 steps to technology identification
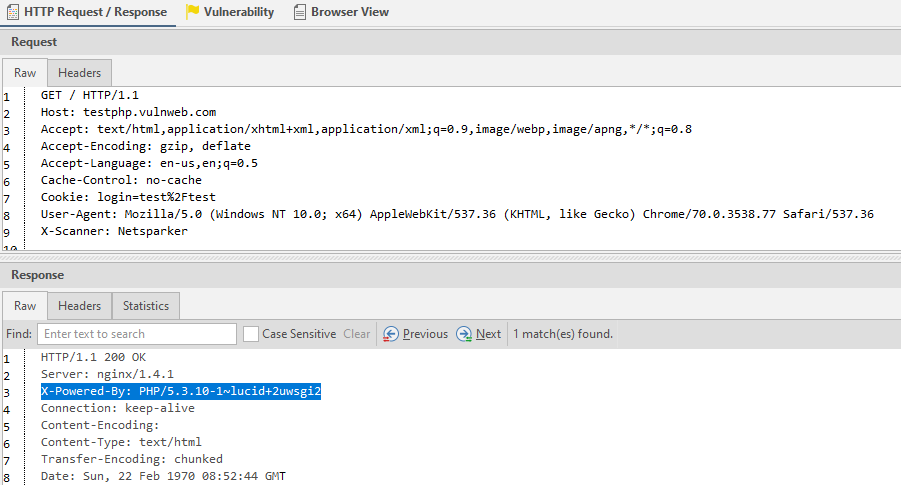
Invicti starts by identifying JavaScript libraries, frameworks, runtimes, web servers, databases, and other components. Successfully identified technologies are reported for your information, and the scanner then attempts to detect the specific versions in use. Any versions that are discovered are reported as version disclosure issues since this information can be useful to attackers. Here is a typical request and response that allows the scanner to identify a specific version: